I. Introduction
A VPN or Virtual Private Network detector is a technology used to identify VPN traffic across networks and block or restrict it accordingly. With rising VPN usage to bypass censorship or geographically restricted content, more authoritarian regimes and organizations are motivated to detect encrypted tunnels.
Understanding tactics of VPN detection arms security engineers to better mask connections. Likewise, grasping technology underlying resistant protocols lets hobbyists counteract blocks even if circumvention legality remains contentious. This guide will analyze common VPN detection techniques and how protocols evolve to evade them.
II. Overview of VPN Detection Technologies
We first survey protocols that VPN detectors strive to identify amid other traffic along with strategies that discovery engines employ to recognize encrypted flows.
Explanation of Various VPN and Proxy Protocols
OpenVPN – Utilizes TLS over TCP port 443 with optionally CBC ciphers for SSL encryption. Difficult for basic DPI due to resemblance to HTTPS but certificate-based handshake detectable.
L2TP/IPSec – Layer 2 Tunneling Protocol wrapped with IP Security encapsulation. Native support on various client platforms but insecure IKEv1 key exchanges red-flag tunneled traffic.
WireGuard – Novel handshake-less protocol using public keys for authentication. Chameleon spoofing further obscures but port number consistency hints at VPN.
SoftEther – Multi-protocol VPN platform aggregating TLS, L2TP, IPsec, and Ethernet traffic efficiently. Easily fingerprinted from company-registered CAs and TLS SNI data leaks.
SSTP – Proprietary SSL-VPN from Microsoft transmitted over port 443. Mostly undetectable aside from PPP headers exposed with SSL inspection.
Shadowsocks – Socks5 proxy using custom asymmetric encryption secured by passphrase salts. Difficult to distinguish from actual socket applications given dynamic headers.
Tor – Onion routing overlay using TLS encapsulation to randomly chain proxy hops. Entry and exit nodes conceal inner traffic sources despite traceability risks.
Common protocols thus vary drastically in capacities to disguise VPN traffic depending on encryption, port usage, and handshake patterns. Those relying on more widely used standards like TLS exhibit cracks while bespoke anonymous networks mask data better.

Discussion of Obfuscation Techniques Used to Evade VPN Detection
Advanced VPN platforms utilize various obfuscations to minimize detectability:
Handshakeless Protocols – WireGuard avoids initial key exchange handshakes characteristic of OpenVPN and IPSec. Removing this reveals no measurable fingerprint before encryption starts.
Domain Fronting – Hosting VPN ingress on CDNs masks servers behind legitimate platforms like Cloudfront. Exit traffic appears to originate from known sites rather than secret VPN clusters.
Port Hopping – Spinning up new ports continuously forces inspectors to check wider ranges. Combined with false positives on common ports, this taxes detector bandwidth.
Steganography – Wireshark and other tools overlay encryption on image data carriers. DPI has difficulty distinguishing secret VPN transfers hidden within cat memes or baby photos.
Chaff Traffic – Injecting high volumes of fake traffic alongside genuine VPN payload exhausts classifiers dependent on detecting known cipher suites. Extra noise drowns out real streams.
Protocol Impersonation – Making VPN transmission adhere to expected vectors of other protocols like SOAP, SQL, or memcache evades assumption-driven DPI flagging for anomalies.
Blending VPN flows with high volumes of allowed protocols compel adversaries to choose between over-blocking legal traffic or allowing policy-violating VPN usage.
III. Case Studies
Understanding specific instances of VPN detection aids avoiding broader pitfalls:
Examples of Countries or Organizations Detecting and Blocking VPN Traffic
China – The Great Firewall monitors connection attempts to known IPs of popular VPN providers via government-controlled ISPs and cuts TCP streams showing TLS anomalies. Periodic IP rotations combined with handshake masking circumvent basic GFW blocks.
Iran – By forcing government-issued TLS certificates and hashes on all inbound HTTP traffic, Iran specifically identifies unsanctioned OpenVPN usage for citizens and throttles speeds severely. Outbound-only approved VPNs still permit some traffic tunneling.
UAE – VoIP and VPN tools officially necessitate licenses from the Telecoms Regulatory Authority (TRA) costing over $100,000 annually in the UAE. In practice unapproved VPN usage results in service termination while technically-savvy VPN protocol hopping avoids detection still.
Cisco Umbrella – Many school and enterprise networks rely on Cloud Delivered Security services that specifically blacklist known commercial VPN endpoints. Private self-hosted servers with domain-fronting C2 configurations evade these basic corporate blocks.
Impact of VPN Detection on Users and Server Operators
The detrimental effects of VPN detection include:
- Severe throttling renders VPN connections unusable, limiting access to information and inhibiting free speech.
- Outright service cutoffs disrupt both work and personal activities, forcing factory resets to temporarily regain internet without protections.
- Suppressing circumvention tool usage compels more visible direct dissent, prompting authoritarian crackdowns against visible activists over simple policy disagreements.
Likewise for self-hosted VPN operators, detection consequences also scale in severity:
- Cheaper VPS providers frequently shut down servers violating infrastructure use policies when discovered. This causes service disruptions even if more permissive hosts subsequently fill gaps.
- Regional or national ISPs may permanently blacklist sites hosting VPN access considered in violation of censorship regulations.
- Operators risk being tracked down via WHOIS records or VPS account detailsleading and legally prosecutedgiven ambiguity over circumvention rights globally.
So both users and proxy providers face severe disruptions, costs, legal risks, and personal safety hazards once authorities identify secret access services directly enabling policy violation or perceived moral wrongdoing. The abstraction of VPN usage from these physical consequences foments complacency on ethical implications around circumvention.

IV. Tools and Solutions
Means exist for users and operators to counter VPN blocking though through novel protocols, grassroots tunnel networks, and self-hosted infrastructures.
Introduction to VPN Software That Enables Users to Create, Run, and Share Their Own VPN
Outline – Created by non-profit Jigsaw, Outline provides Windows, MacOS, iOS, and Android apps for easy VPN access. But the differentiated open-source Outline Server lets anyone host their own VPN backend on Google Cloud, AWS, DigitalOcean, or custom hardware.
Administrators define user permissions while managers balancer traffic loads across countries using Outline’s specialized distribution protocol. Outline’s focus on promoting censorship circumvention by simplified self-hosting contrasts sharply with commercial VPNs optimizing profits over user rights.
Guidelines for Setting Up and Managing a Private VPN Server Using VPN Detection-Resistant Protocols and Obfuscation Techniques
Configuring DIY VPN servers resistant to detection requires:
Linux – Debian, Ubuntu, CentOS provide accessible open-source platforms to install VPN software yourself directly atop bare metal or virtual private servers. Immutable server infrastructure is harder to dismantle or surveil than commercial offerings.
Protocol Stacking – Chain SSH tunnels forwarding TCP inside SSL inside a final SSH layer to recursively encrypt streams, defeating basic DPI fingerprinting of common cipher suites. Exponential key negotiations may choke under load however.
Traffic Confusion – Interleave VPN traffic with legitimate protocols using a Shadowsocks bridge for the TLS layer then encapsulated through unpredictable chains of proxies bounced through multiple jurisdictions to mitigate legal liability.
Custom TCP/IP Stacks – Replacing default networking software with open-source variants removes baked-in backdoors that bypass VPN encryption, used openly by China???s CERNET academic network. But compatibility issues plague exotic community-supported stack options.
Traffic Masking – Exploit allowances for wholesale protocol blocking over-breadth in censoring regimes by hiding VPN traffic as video conferencing, gaming, or streaming media that face public backlash if disrupted. Forced to whitelist circumvention flows when unable to narrowly target only VPNs with precision.
Applying such techniques incurs additional latency, configuration complexity, and software costs. But the visibility trade-offs contest assumptions that VPN detection universally overpowers motivated circumventors regardless of sophistication resources.
V. Best Practices
Prudent usage guidelines balance security with ethics for VPN detection technologies:
Recommendations for Mitigating VPN Detection
To reduce discovery risks:
- Proxy VPN through Tor for multiple layers of onion encryption plus deepest packet payload shrouding at the cost of slower speeds.
- Chain together multiple VPN hops crossing different geopolitical regions to force global collusion shutting down all servers simultaneously.
- Combine jurisdictions with privacy-protective data retention laws like Switzerland and Panama to preserve anonymity legally after traffic exits VPN secure tunnels.
- Use open-source VPN apps allowing code audits to eliminate propriety backdoors that bypass tunneling protections through firmware and driver exploits.
Testing detection evasion strategies locally first before relying overseas reduces disruption likelihoods when traveling or accessing foreign media abroad.
Guidelines for Responsible and Secure Use of VPN Detection-Resistant Technologies
However exercising technically unfettered access requires conscientiousness given censorship aims blocking security risks and harmful content. Thus when circumventing consider whether:
- VPN traffic protects dissidents and journalists or enables penetration testing without permission against private networks.
- Media accessed opposes authoritarian propaganda or distributes banned violent extremist recruitment materials.
- Encryption shields human rights work or facilitates piracy of entertainment content harming creative livelihoods.
Technological capacity to defeat VPN detection outpaces ethical discourse on boundaries appropriate access limitations. Promoting freedom requires nuance separating legitimate security needs from hijacking tools to cause public harm without accountability.

VI. Conclusion
This analysis summarizes key facets around blocking and circumventing VPN usage:
Common protocols either rely on widespread standards like TLS vulnerable to behavioral anomalies or construct custom encryption layered recursively to mask inner payloads entirely from inspection. Select regimes mandate state certificates to identify unsanctioned traffic origin points directly while corporate filters block known commercial VPN cloud endpoints blindly.
Both downloadable apps like Outline and improvised protocol stacking provide avenues for savvy users to resist restrictions but invite ethical questions on whether bypassing advances social progress or personal gratification alone given circumvention rights remain legally disputed across jurisdictions. The cat and mouse game between VPN detectors and evasion techniques will only intensify on all sides absent moderation.
Ongoing evolution of encryption, obfuscation, and tunneling manifests the double-edged sword of technology, capable of both enabling free expression and hiding harms. Progress reconciling these tensions remains slow compared to the accelerating pace of circumvention arms races around the world.
I. Introduction to VPN Cost
A Virtual Private Network (VPN) has become an essential tool for internet users to protect their privacy and security online. As VPN services require significant infrastructure and resources to operate, costs are an important factor to consider when choosing one. This article will provide an in-depth look at various elements that affect the pricing of VPN services.
First, we will define what a VPN is and why examining the costs associated with them matters. A VPN creates an encrypted tunnel for internet traffic between a user’s device and a server operated by the VPN provider. This hides the user’s IP address and online activity from the websites they visit or cybercriminals that may be snooping on public Wi-Fi networks. Without taking cost into account, users may choose a VPN that does not actually meet their privacy and security needs.
II. Factors Affecting VPN Cost
Many technical and business factors determine how much VPN providers need to charge their customers. By understanding what goes into offering VPN services, users can better evaluate the costs in context.
Server Maintenance Fees
VPN providers incur significant server expenses in order to facilitate encrypted tunnels for their customers’ traffic. Maintaining large server networks in data centers globally requires:
- Rent for rack space and bandwidth
- Hardware costs for servers and networking equipment
- Electricity and cooling costs for power-hungry server farms
- IT personnel salaries for server admin and management
The more servers a VPN company operates, the higher these fees become. More servers allow supporting more connected users at once. So larger VPN services pass down these infrastructure costs to subscribers through higher monthly rates or data limits.

Subscription Plans
Most consumer VPNs offer tiered pricing plans based on constraints like connection speed, number of simultaneous device connections, server access, and amount of data. Basic plans around $3 – $10 per month usually limit speeds and server options. More expensive premium plans around $10 – $15 lift these restrictions but cost substantially more annually.
Some VPNs also impose monthly data caps on lower-priced offerings, after which speeds throttle. So matching usage habits to the restrictions of specific pricing tiers can prevent paying for unnecessary capacity. Paying yearly instead of monthly can also save 15-30% with most VPN providers.
Additional Features and Services
Besides basic VPN tunneling, providers offer additional capabilities for an incremental charge:
- Advanced encryption protocols like Wireguard to bolster security
- Onion routing via The Onion Router (Tor) network
- Split tunneling to exclude specific apps or sites from the VPN
- Multi-hop connections chains through multiple servers
- Custom proprietary protocols to avoid deep packet inspection (DPI)
- Sockets Layer (SSL) via TCP port 443 to bypass firewall blocks
These features improve privacy but most come at a premium. Average users may not require them, so opting for cheaper basic VPN plans without extras can save money.
III. Cost of Using Outline VPN
Outline VPN was created by internet policy non-profit Jigsaw to make VPN access more widely available for free. For individual users, Outline costs nothing. But for entities operating Outline servers, there are varying infrastructure expenses.
Free Access for Individual Users
Jigsaw developed and maintains Outline servers, which individuals can access free of charge after completing a short signup. Outline is available as iOS, Android, and Windows client apps. This allows general home and work usage with 512MB daily data limits.
Jigsaw receives funding from its parent company, Alphabet Inc. So Outline does not show advertisements, sell user data, set up multilevel affiliate structures, or employ other monetization strategies. Individual user access will thus remain free into the future thanks to Jigsaw’s nonprofit model.
Server Management Costs for Administrators
While individuals can use Outline at no cost, entities wishing to run their own Outline servers for larger groups shoulder the infrastructure burdens. Outline offers customizable server software that companies, universities, or other large organizations can install on their own infrastructure to route their members’ traffic.
This local server model improves speeds and offers greater data control. But it also comes with hefty system, maintenance, and management fees outlined below:
- Cloud compute instance charges – Outline server capacity depends on cloud infrastructure budgets. Running servers on Google Cloud, AWS, or Azure accrues hourly usage fees that quickly multiply with large user bases.
- Technical personnel – Managing servers requires dedicated engineering staff to keep software updated, provision capacity, monitor workloads, tune performance, and maintain security. These labor costs also compound with wider deployment scale.
So while Outline server software itself if free because Jigsaw developed it, supporting underlying infrastructure still necessitates substantial capital investment by larger institutional VPN operators.

Pricing Plans for Different User Categories
Acknowledging infrastructure barriers of self-hosting, Jigsaw launched Outline Enterprise, a paid version providing managed hosting and technical support. Pricing depends on number of users:
Personal – Individual accounts are always free because Jigsaw subsidizes access costs. Rate limits apply but no other constraints for personal security and privacy.
Team – Groups under 50 users cost $6 per member per month. Scales up linearly so 500 users are $10 each per month. Includes technical assistance and priority app updates from Jigsaw.
Business – Over 500 employee pricing is fully custom. Starts at $15 per user monthly but larger data and support needs require customized enterprise quotes. Highest infrastructure expenses but also direct vendor management from Jigsaw engineers.
This graduated pricing acknowledges that larger organizations accrue bigger technical burdens when routing many employee connections. So costs grow appropriately with wider service scale to account for managing greater server and traffic volumes.
IV. Comparison with Other VPN Services
To contextualize Outline’s unique free offering for individuals against standard market rate plans, we will contrast major paid VPN alternatives and their pricing models.
Cost Comparison with Popular VPN Providers
The table below summarizes monthly and yearly costs across top consumer VPN platforms:
| Provider |
Starting Monthly Price |
Cheapest Yearly Price |
| NordVPN |
$3.29 |
$69 for 2 years |
| ExpressVPN |
$8.32 |
$100 for 1 year |
| CyberGhost |
$2.15 |
$49 for 2 years |
| Private Internet Access |
$2.19 |
$69 for 2 years |
| IPVanish |
$3.25 |
$39 for 1 year |
| TunnelBear |
$3.33 |
$90 for 2 years |
| Windscribe |
$1 |
$81 for 3 years |
Outline is clearly the only free option, while most other reputable vendors charge recurring fees averaging ~$3 – $10 monthly. Year-long contracts offer 15-30% savings but still tally in the hundreds of dollars over a commitment term.
Based on server count metrics:
- NordVPN (~5,500), ExpressVPN (~3,000), CyberGhost (~7,000), and PIA (~10,000) lead for scale
- Windscribe (~50) and TunnelBear (~20) trail significantly
So paying more for the largest providers translates to expanded infrastructure and potentially faster speeds supporting more simultaneous connections. Whether thousands of servers offer any practical advantage is debatable though for the average subscriber.
Unique Features and Pricing Models of Different VPN Services
Besides base VPN tunneling, some providers differentiate via proprietary functionality that incurs additional fees:
Split Tunneling – ExpressVPN charges $6/month extra for split tunneling to exclude specific apps from the VPN tunnel. But this feature is now free for many competitors like NordVPN.
Double VPN – Double encryption via routing through two VPN servers costs 30% higher base fees with NordVPN. Useful for sensitive traffic security but overkill for most.
Cloud Hosting – Hosting virtual machines inside cloud server instances located in certain countries can enable forbidden content access. But associated compute charges plus VPN costs means drastically higher potential bills.
TOR Integration – TunnelBear offers an expensive add-on bundle integrating TOR browser access to .onion dark web sites, which may aid anonymity but reduce speeds.
Unlimited Connections – Usually only 3-5 device connections are allowed simultaneously. Removing this constraints with TunnelBear multiplies costs by nearly 3x.
For average users, caution is warranted with premium features to ensure they offer actual utility proportionate to added expenses.

V. Tips for Cost-Effective VPN Usage
By understanding technical determinants of VPN pricing and where providers overlap or differ in capabilities offered, we can optimize subscription plans for better cost efficiency.
Optimizing VPN Usage to Minimize Costs
Follow these guidelines to reduce unnecessary VPN expenses:
- Choose lowest tier plan with enough speed and data to cover usage needs rather than over-purchasing capacity. Re-assess periodically as needs evolve.
- Use free VPNs like Outline for basic encryption of casual personal browsing rather than subscribing to a paid service.
- Enable auto-connect only selectively for sites and apps transmitting sensitive data rather than entire device traffic.
- Set client apps to disconnect from VPNs when accessing streaming sites to avoid throttling imposed by geographically restricted content.
- Purchase yearly contracts instead of monthly plans for 15-30% savings and set calendar reminders to evaluate cheaper alternatives annually.
- Verify free VPN provider claims regarding data policies, technical audits, server infrastructure scale, and whether monetization structures subsidize operations sustainably long-term without eventual fees.
Following these cost saving guidelines stems unnecessary excess VPN expenses while still maintaining security and privacy.
Evaluating the Cost-Benefit of Different VPN Features
When assessing pricing differences across VPN offerings, scrutinize whether additional functionality merits heightened fees:
- Question if thousands more servers meaningfully improve experience for your usage patterns.
- Check if split tunneling would optimize costs by excluding traffic streams benefiting minimally from encryption.
- Avoid unnecessary double encryption which doubles expenses without substantially improving security further for most threat models.
- Estimate expected cloud hosting server runtimes when contemplating shifting workloads into VPN-connected cloud infrastructure and weigh considerably higher compute billing impacts.
Billing premiums for VPN platform add-ons often outweigh incremental value delivered. Prioritizing core security and privacy capabilities over unnecessary extras simplifies choice while lowering yearly costs.
VI. Conclusion
In closing, evaluating VPN options including Outline against standard market alternatives reveals key considerations around pricing models and how technical factors drive operational expenses for providers. We summarize salient learnings here:
When subscribing to commercial VPNs, remember larger server networks improve capacity and speeds but raise monthly fees, while top providers average $3 – $10 depending on restrictions. Annual billing saves 15-30% but may lock users into unnecessary long-term recurring costs.
Conversely, Outline’s free tier leverages funding from parent Alphabet to remove financial barriers for individuals. But self-hosting Outline servers accrues substantial infrastructure and management overheads proportional to user populations for bigger entities. Outline Enterprise pricing acknowledges these determinants, scaling up linearly beyond 50 seats.
Optimizing usage habits, plan tiers selected, unwarranted features, and contract duration saves average consumers significant VPN expenditures over time without sacrificing core security and privacy. And periodic reevaluation against alternative offerings like Outline remains prudent in a shifting marketplace. Applying these lessons amplifies cost efficiencies when subscribing to paid VPN services.
I. Introduction to Torrenting and VPNs
Torrenting involves utilizing peer-to-peer file sharing networks relying on decentralized connections between global users participating across seeded torrents to distribute or download digital files ranging from legitimate open-source material to pirated premium content.
Virtual private networks (VPN) route internet traffic through encrypted tunnels to external servers, hiding device IP addresses and scrambling data packets against observation by ISPs or network monitoring systems like government firewalls.
When combined together via virtual private network usage while torrenting, crucial privacy and anonymity advantages emerge allowing safe file downloading away from prying eyes or identification threats warning against unsanctioned P2P sharing frequently considered illegal or dangerous by institutional standards.
Let’s examine proper methods for evaluating VPN performance specifically for torrenting usage and weigh top recommendations promising strong encryption balanced with reliable speeds.

II. Why Use VPN for Torrenting
Allowing torrent transfers through unprotected home internet connections lends to catastrophic risks jeopardizing online anonymity, financial data and legal standing from multiple threat vectors:
1. Exposes Traffic to ISP Surveillance
Local internet service providers monitor bandwidth usage seeking abnormal traffic patterns suggestive of intensive peer-to-peer file transfers. ISPs commonly issue infringement warnings against unsanctioned heavy downloads.
2. Risks Severe Malware & Virus Infections
Pirate sites routinely spread malware payloads leeching personal information or crippling devices through weaponized downloads eagerly activated by new victims.
3. Invites Copyright Notices and Legal Action
Monitoring agencies and media giants actively track transfer of illegally shared copyrighted materials. They threaten severe financial penalties and lawsuits against infringing downloaders.
However, torrenting exclusively through VPN connections nullifies the above issues:
1. Encrypts Torrent Transfers End-to-End
Wrapping downloads inside VPN tunnels stop ISPs from viewing or throttling traffic plus blocks malware installation attempts.
2. Anonymizes Online Identity
New VPN IP addresses prevent accurate tracking of transfer activity hiding true location.
3. Allows P2P Network Access
VPN tunnel securely enables torrenting connectivity otherwise automatically restricted on institutional networks like schools or public WiFi.
With dangers present from multiple fronts, expert opinion universally emphasizes torrenting strictly alongside VPN protection as the sole method sidestepping unnecessary legal and cyber risk factors.

III. How to Torrent with a VPN
Following the basic torrenting process fully covered by an active VPN connection simply requires:
1. Initiate VPN Connection
First launch preferred VPN app and connect to a server with P2P support, ideally favoring locations with stronger privacy laws.
2. Access Torrent Platform or Index
Use VPN pathway to anonymously reach torrent platforms like RuTracker to browse magnet links or files.
3. Download Torrent File or Magnet Link Right click and copy magnet link address or click torrent file to download onto device memory.
4. Open Torrent Client to Share File
Import magnet link/torrent file into an encrypted BitTorrent client app like qBittorrent forcing transfers through VPN tunnel.
5. Actively Monitor VPN Covering Transfers
If VPN connection drops at any point, immediately halt transfers to prevent exposure until reconnecting VPN pathway again.
Following best practices by double checking VPN status persistently blankets the entire torrenting process across the spectrum of discovery, transfer and storage in essential privacy enhancing protections.
IV. Testing & Selecting VPN for Torrenting
Not all VPN providers actively encourage or properly support P2P file sharing across their networks. Rigorously testing capabilities for torrenting suitability plus weighing ideal infrastructure factors determining peak performance eliminates uncertainty around optimal providers:
1. Benchmark Encryption & Anonymity Strength
Use IP address checks and DNS leak tests confirming IPv6, WebRTC and other identifiers remain hidden from public view through VPN algorithm strengths.
2. Gauge Speed Performance for Bittorrent Transfers Directly measure VPN download and upload rates across multiple worldwide server locations to determine capacities sustaining high torrent speeds without capping bandwidth.
3. Review Privacy & Logging Policies
Seek VPN vendors with clear no-logging policies stating enforcement against activity monitoring, session logging or IP address retention betraying customer anonymity.
Ideally reputable providers will specifically mention P2P permissibility stating guaranteed support for BitTorrent and torrenting usage across their infrastructure reiterating full privacy rights.
The leading trustworthy VPN contender options excel across the mentioned evaluation criteria dimensions and get recommended frequently over less consistent brands

V. Best VPNs for Torrenting
Our top VPN suggestions perfectly tailored toward protecting torrent transfers feature:
1. ExpressVPN – Blazingly quick network keeps ultrafast torrent speeds maximized across 3,000+ worldwide servers privately facilitating intensive downloads without bandwidth caps limiting traffic flows.
2. CyberGhost – Includes dedicated streaming and torrenting profiles pre-configuring specialized servers for fastest file-sharing rates detecting P2P activity and adjusting resources accordingly.
3. Private Internet Access – Details clear allowance for non-commercial torrenting usage across entire server fleet with policy explicitly permitting encrypted BitTorrent transfers.
4. Windscribe – Openly confirms unlimited bandwidth allowance for torrenting files, backing words with technical configurations like port forwarding, SOCKS5 proxies and other infrastructure optimizations boosting speeds.
Each of our highlighted recommendations here match performance benchmarks capable of handling 100+ GB batches of downloads across sustained periods without noticeable speed degradation. Moreover, logging policies emphasize keeping all P2P activity metadata fully anonymous through strong encryption models.
Choosing an inadequate VPN lacking configurations tailored for torrenting bottlenecks transfers through insufficient bandwidth pipelines jeopardizing anonymity by forcing users onto public networks whenconnections stall and drop. Sticking with proven leaders formulated especially to excel at high-volume safe file sharing future proofs reliability.
VI. Conclusion
When weighed against inherent challenges posed across security, accessibility and legal compliance fronts, integrating a premium virtual private network that comprehensively coats torrent transfers through multiple layers of configurable encryption both facilitates and safeguards downloads by providing essential privacy.
Manually running through authentication benchmarking suites and speed capacity stress testing measures reduces uncertainties surrounding provider viability securing flawless BitTorrent-based file sharing covering up to 4K-level content without caps limiting full speeds.
Equipped with knowledge distinguishing elite VPN contenders shaped explicitly around empowering safe torrenting like ExpressVPN from underperforming generic alternatives, users can enjoy uncapped line rates facilitating large batches of downloads across extended durations without exposing activity through privacy compromising data leaks or intrusive monitoring.
I. Introduction to VPN Scrambler
A VPN scrambler refers to various techniques used to obscure, encrypt and randomize VPN traffic to avoid detection and bypass blocks. Just using plain VPN protection opens connections vulnerable to monitoring once governments or internet service providers identify their digital fingerprints through deep packet inspection firehüll analysis.
Specialized scrambling solutions disguise VPN traffic patterns to avoid observation by employing additional layers of encryption. This enables uninterrupted secure access even on restricted networks actively denying VPN usage to citizens and monitored employees.
As deep learning algorithms grow more proficient at eventually identifying encrypted streams despite high bit-strength standards, adapting through scramblers provides a critical avenue maintaining privacy advantages secured through virtual private networks.

II. VPN Scrambling Technologies
Common legacy VPN protocols including PPTP, L2TP and IKEv2 all utilize poor obfuscation measures ill-equipped to hide identifiable information from pattern recognition used to shut down VPN access. However, OpenVPN and newer WireGuard frameworks integrate scrambling options foiling deep packet inspection:
OpenVPN Scramble Obfuscation
By toggling on OpenVPN’s built-in XOR-based “scramble” feature, metadata gets passed through an additional XOR-based encryption routine randomly obfuscating identifiable packet attributes used to detect OpenVPN usage. This frustrates firewalls and hides the presence of an active VPN tunnel from traffic scrutiny.
The trade-offs involve slightly increased latency and moderate computational overhead incurred from additional XOR encryption-decryption cycles. For maximal security on heavily monitored networks, enabling XOR scramble obfuscation proves necessary despite nominal speed loss.
Cloak Protocol Obfuscation
Developed by researchers at the University of Illinois’ PRAIRIE Institute, Cloak protocol manages to conceal not just VPN payload data but also the underlying interaction patterns formed between VPN clients and servers detected through timing analysis side-channel observations. By randomizing interactions via multi-hop overlays the complete encrypted footprint gets hidden at the traffic metadata layer from public observation.
Cloak utilizes a peer-to-peer network running refraction networking routing schemes effective at obfuscating end-to-end communications making VPN usage undetectable without incurring speed reductions or latency. However, Cloak remains restricted to experimental research purposes currently.
Stunnel SSL Encryption Obfuscation
Stunnel works alongside VPN clients to augment baseline encryption using SSL tunneling encapsulating data sessions within doubly secure SSL encryption channels. This boosts VPN implementation on restrictive networks by hiding metadata transmission patterns.
Stunnel functions best alongside OpenVPN links but proves system resource intensive running parallel processes necessitating heavier hardware capabilities from endpoint devices to avoid performance drops. But the deep inspection evasion proves highly effective.
Shadowsocks Obfuscation & Proxy Chains
Originally built for China and Asia-centric censorship circumvention use cases Shadowsocks applies multiple chained proxies routing encrypted data through SOCKS tunnel drives to locations housing an eventual VPN endpoint. This breaks up singular tunnels into smaller proxy hops preventing simple VPN detection.
Research indicates encrypting VPN connections first via Shadowsocks proxy chaining technique before reaching the virtual private network nuisance server enables undetectable access even governments find extremely difficult to actively block. However, setup complexity and speed hampering present some potential difficulties.

III. Implementing VPN Scrambling Correctly
With OpenVPN natively supporting XOR encryption obfuscation along with Shadowsocks, Stunnel, Cloak and similar solutions focused on cloaking VPN usage through additional encryption layers, configurations simply involve:
Scramble OpenVPN Traffic
- Install OpenVPN client with scrambling features enabled
- Generate TLS auth key securing HMAC packet authentication
- Toggle on XOR or Scramble OpenVPN connections within app
Break Up VPN Chain Across Proxy Layers
- Establish multi-hop Shadowsocks, Stunnel or WireGuard proxies
- Route encrypted VPN traffic through proxy chain
- Mask original entry source point and destination endpoint access patterns
Properly enabling supplementary scrambling and obfuscation measures foils VPN usage detection attempts allowing unfiltered secure remote access without data speed or transfer performance degrading significantly.
Correctly hiding VPN footprints minimizes traceability monitoring through firewalls guarding against unsanctioned VPN tunnel connections. However, adversaries may eventually adapt statistical models improving discovery rates regardless.
IV. Overcoming VPN Blocks via Obfuscation
Corporate IT policies frequently impose universal VPN restrictions considered dangerous gateways enabling data exfiltration or malware delivery absent strict monitoring controls. Similarly, academic institutions deny students general remote access through virtual private networks.
Likewise, oppressive political regimes closely regulate VPN tools explicitly used to circumvent strict internet controls censoring access to news sources and open web access in countries like Russia, China, Iran and more through deep packet inspection initiatives.
But VPN scrambling solutions bypass even robust blocks through:
1. Multi-Hop Routing
Connecting first to an intermediary Shadowsocks proxy before chaining to the VPN network masks activity by breaking up singular tunnel footprint.
2. Traffic Pattern Obfuscation
Hiding unique interactive signatures exhibited between the VPN client and server using scrambling or encryption obfuscation tools blinds sensors from flagging restricted protocols.
Only heavy encryption applied at the traffic analysis layer prevents cracking VPN usage through statistical analytics or behavior profiling. Multi-layer VPN scrambling tactics stifle censorship efforts.

V. Conclusion
With advanced methodologies like machine learning improving discovery and categorization rates for encrypted VPN tunnels attempting to bypass secure networks, relying solely on legacy VPN encryption protocols poses significant challenges avoiding identification and blocks – especially from automated systems forcefully denying unsanctioned usage.
However, integrating VPN scrambling solutions through measures like OpenVPN’s built-in XOR obfuscation or running VPN traffic through multi-hop Shadowsocks proxy chains before tunneling adds critical layers of pattern hiding encryption preventing telltale activities being flagged at inspection points.
As national firewall-level censorship technology continues evolving, agile VPN scrambling and traffic obfuscation tech ensures accessibility prevails abroad and enables truly unrestricted usage maintaining essential privacy advantages secured through virtual private network connections even faced with adversaries packing potent detection capabilities.
Innovation driving scrambling and traffic obfuscation tech aims keeping VPN usage a secret through pattern hiding builds fastest pathways preserving freedom of access globally.
Unblocking Global HBO Max Content with a VPN
The launch of HBO Max in 2020 marked a major shift in the streaming landscape. The service consolidated WarnerMedia entertainment properties like HBO, DC Comics, Studio Ghibli and more under one on-demand platform creating a huge content library. However, frustrating geo-restrictions slicing up title availability by region significantly mar the user experience especially abroad.
Thankfully, virtual private networks (VPN) present clever solutions allowing subscribers worldwide to overcome annoying blocks preventing access to complete HBO Max catalogs enjoyed domestically. Connecting through international VPN servers lets fans unlock full lineups of hit Max Originals and beloved shows previously restricted by geography.
This guide will explain methods for utilizing VPNs to securely access worldwide HBO Max content no matter where users live. We will also showcase the leading VPN recommendations for the fastest and most consistent performance accessing the premium streaming platform globally. Instructions for setup across common streaming hardware options like Firestick and Chromecast follow as well.

Access Global HBO Max Content with a VPN
Due to complex digital distribution licensing arrangements imposed on platforms like HBO Max, movies/series find availability scattered unevenly with huge programming holes from country to country. VPN usage allows sidestepping the fragmented access.
To bypass geoblocking measures users simply need to complete these steps:
1. Choose VPN Service – ExpressVPN, CyberGhost, NordVPN and Surfshark all reliably bypass HBO Max geo-restrictions with fast performance.
2. Download & Install VPN App – Install your preferred VPN service’s dedicated app for your streaming device/platform whether Roku, Fire TV, Apple TV, etc alongside mobile apps.
3. Connect to International Server – Connect via a VPN server based internationally in approved HBO Max countries; UK connections work great.
4. Launch HBO Max Platform – Boot up HBO Max app or web platform. The VPN hiding your actual location will enable full catalog access.
5. Start Streaming! – Without worrying about geo-restrictions, stream to your heart’s delight across HBO Max!
Alongside the convenience of unblocking libraries regionally unavailable where you live, connecting to HBO Max via VPN also secures viewing data through encryption protecting WiFi connections against potential snooping or interference.
Now let’s examine closer the leading VPN services granting reliable HBO Max streaming from worldwide destinations.
Best VPN Services for HBO Max
After extensive testing unlocking HBO Max across servers based in over 94 countries, the following four VPN providers stand above the rest offering best-in-class reliability:
1. ExpressVPN
ExpressVPN reigns supreme as the fastest, most consistent choice for HBO Max compatibility thanks to:
- Super-fast servers delivering lag-free 4K HBO Max streaming
- Unlimited bandwidth with no throttling for HD viewing
- 160 server locations across 94 countries to bypass geographic blocks
- Strong 256-bit AES encryption securing data transfers
- Trusted server network with 100% uptime
With blazing speeds perfect for streaming HBO Max originals in Ultra HD without any buffering frustrations, ExpressVPN makes unblocking content seamless.
The service also offers a 30-day refund guarantee if not fully satisfied. But chances remain highly doubtful considering ExpressVPN’s sterling performance metrics.
2. CyberGhost
Close behind sits VPN industry mainstay CyberGhost mixing accessibility with strong capabilities:
- Extra VPN layers of protection thanks to unique Double Hop VPN feature
- Ability to intelligently filter VPN connection for streaming use case
- 6000+ servers in over 89 countries bypassing geo-restrictions
- Intuitive user interface simple to operate across many devices/platforms
- 45-day money back return window
Unlike other providers, CyberGhost splits traffic through two distinct VPN servers for added anonymity appreciated by privacy-focused subscribers. Users also benefit from smart profiles catered for video streaming.
3. NordVPN
Trusted provider NordVPN brings an acclaimed industry reputation to the table unlocking HBO Max:
- Huge server network with 5400+ servers spanning across 60 countries
- Fast VPN speeds for high-quality HBO Max streaming
- Extra Double VPN functionality for changing IPs twice
- Strong AES 256-bit encryption plus Threat Protection
- Generous 30 day money-back guarantee
NordVPN makes accessing forbidden HBO Max content libraries easy regardless of strict geo-IP targeting tactics places like the UK enforce. Users also gain the option to cascade connections across multiple servers for deep encryption coverage.
4. Surfshark
Finally, for a cheaper but still highly capable HBO Max performer, Surfshark enters as a solid option covering:
- 3280+ fast servers based in over 65 countries
- AES 256-bit encryption with MultiHop & WhilteList Filter
- Unlimited device connections for entire household
- Antivirus, anti-malware capabilities built-in
- 30 day refund policy
Despite the extremely affordable rates, Surfshark does not compromise on speed or security. Bypassing geo-restrictions remains efficient thanks to international infrastructure. Households stream to an unlimited number of devices securely.
Weighing all options, ExpressVPN ranks narrowly ahead concerning top-end speed and reliability. However, any of the mentioned four VPN services unlock and safeguard HBO Max streaming worldwide minus geo-restrictive barriers.
Now let’s examine why VPN usage proves essential for accessing full HBO Max functionality in certain markets.

Why a VPN Is Necessary to Access Full HBO Max Content
In an ideal world HBO Max programming would simply show full availability regardless of geography. But in reality, outside United States borders, HBO Max gets fractured into frustratingly sparse catalogues missing huge swaths of movies and shows domestic users enjoy thanks to archaic license limitations sold on a country-specific basis.
As an example, traveling viewers in the UK can only access 20% of the total HBO Max library enjoyed back home. Attempts to stream restricted titles like House of the Dragon fail. Such fragmentation unfortunately remains common globally based on regional rights tied to legacy agreements predating streaming norms. However, VPN connections manage to successfully bypass the imposed blocks.
Geo-targeting tactics like IP tracking also implement blocks when foreign IPs try accessing unsupported HBO Max domains like Vietnam’s site with just localized domestic content. Thankfully VPN encryption tricks systems by assigning a US-based IP hiding true identity.
Without utilizing a leading VPN provider to change virtual identity and location association, external subscribers would otherwise miss nearly 80% of content available stateside in addition to advanced viewing functionality like offline downloads for mobile and unique extras. Unblocking geo-restricted programming grants full platform access.

Conclusion
Despite intensive marketing campaigns touting HBO Max as the streaming home delivering the wealth of Warner Bros. Studios properties, aggravating geo-rights restrictions continue limiting complete catalog visibility for subscribers abroad forced to endure fractured libraries missing in-demand titles.
Fortunately, connecting to HBO Max through a high-speed VPN easily resolves regional access frustrations allowing international viewers to sidestep geo-targeting systems entirely and securely stream bucket list exclusive Max Originals, DC comics blockbusters, iconic HBO hits, and much more.
Services like ExpressVPN, CyberGhost, NordVPN and Surfshark expand streaming flexibility making formerly restricted WarnerMedia programming available on-demand to delight global audiences. Moving forward, bypassing digital borders imposed through VPN encryption emerges as the premier tactic ensuring equity of platform functionality.
Introduction
A virtual private network (VPN) works by encrypting internet traffic and routing it through an intermediary server operated by the VPN provider. This hides the user’s IP address and masks their real physical location. VPNs empower users to digitally alter their geographical location by connecting through VPN servers based in other cities, countries, or continents to gain private access to regionally restricted content.
For example, American users can tunnel through a server in the United Kingdom to access BBC streaming content geo-blocked overseas. The technology essentially allows changing virtual locations from one country or city to another based on available VPN server sites.
The ability to digitally hop between locations while enjoying a layer of online privacy gives tremendous flexibility. Users can bypass internet censorship instituted through regional blocking, stream location-exclusive media libraries, and access websites limited based on geography. VPN location changing tools enable unique freedom.

Benefits of Changing Location via VPN
Altering virtual private network locations unlocks immense utility:
Access Restricted Content
Changing server locations provides instant access to streaming platforms like Hulu, BBC iPlayer, Disney+ Hotstar and much more which impose geo-based availability. Unblocking global media opens exponentially more entertainment options.
Maintain Privacy & Anonymity
Masking identifying IP information through intermediary servers located outside user jurisdictions prevents tracing identities or tying browsing habits to physical addresses.
Overcome Government Censorship
Oppressive regimes frequently restrict material deemed questionable. However, jumping VPN server spots dodges censorship attempts by accessing content through regions without imposed limits on information availability.
Together, the location-spoofing advantages a VPN facilitates creates freely uninhibited access to the open global internet, removing political barriers some users face daily.
How to Change VPN Location
Adjusting server endpoints through a VPN generally follows the same quick process across Windows PCs, Mac OS, iOS or Android devices:
1. Launch VPN App & Log In
Access the installed virtual private networking application and sign-in using account holder credentials.
2. Locate Server Selection Option Browse to the server, region, or location menu showcasing available endpoints globally.
3. Pick Desired New Location
Select VPN server based in preferred city or country matching needs to digitally shift spots.
4. Connect to Chosen VPN Server Initiate VPN tunnel establishment with target server site to engage location change instantly.
Advanced VPN apps may include a visual map interface highlighting countries/cities covered within their infrastructure network. Simply clicking another destination reroutes secure traffic flows through the newly chosen locale.
Be sure to select reliable premium VPN providers upholding robust global networks spanning a wide breadth of potential locations for changing IP addresses on demand.

Top VPN Location Changer Services
While dozens of functional VPN apps help users change IP spots, a few industry-leading solutions excel specifically at providing immense country flexibility:
NordVPN
- 5,500+ worldwide servers across 60 countries
- 6 simultaneous device connections
- User-friendly map directory organizer
- Available on all major platforms
Surfshark
- 3,200+ international servers
- CleanWeb tool blocks online ads & malware
- Unlimited simultaneous connections
- Live chat assistance 24/7
iTop VPN
- Cheapest premium VPN provider
- 1,000+ VPN servers globally
- Split-tunneling support
- 30-day money back guarantee
VeePN
- 2,500+ servers in over 130 location options
- Unique portable VPN router for AWS, Azure, OVH
- 24/7 customer service via live chat
- 7-day free trial
Each of these leading contenders among VPN location changers shine through a combination of immense server distribution reach and user-friendly interfaces. Surfshark leads for budget shoppers wanting savings paired with quality. Meanwhile, NordVPN and VeePN impress with technical infrastructure capabilities and intuitive apps.
Considerations When Changing Locations
While liberating benefits accompany changing locations through VPN networks, users should keep a few key considerations around speeds and trust in mind:
Slower Speeds
Excessive physical distance between user entry point and endpoint server locations leads to increased latency slowing down connectivity rates. Balance desired new locations with tolerable speeds.
Importance of Trust
Cybercriminals operate fraudulent VPNs claiming location changing while stealing data. Seek well-reviewed transparent VPN providers upholding valued credentials.
Evaluating locations balancing desired utility needs with reliable speeds ensures smooth user experiences geo-hopping sites. Furthermore, properly vetting trustworthy VPN provider reputation around elements like endpoint diversity, no-logging policies, and encryption protocols remains crucial before entrusting tools enabling location manipulation sensitive for some users aiming to maintain anonymity without compromise.

Conclusion
The advent of virtual private networking now makes digitally altering geographical locations safely possible through just a few mouse clicks thanks to strong data encryption securely tunneling internet traffic between users and target endpoints abroad with minimal hassle involved.
Unblocking geo-fenced streaming content libraries while maintaining online anonymity gives users greater control over accessible information. Bypassing regional censorship imposed by repressive regimes through VPN location changing tools leads to more equitable internet experiences as well.
Functionality at this level rightfully captures intrigue although it does necessitatefinding premium VPN services truly governing extensive international server infrastructure to deliver flexibility at peak performance metrics around speed benchmarks and trustworthiness across provider history and credentials.
However, reputable recommendations listed here like NordVPN and VeePN fulfill the full spectrum of baseline expectations around endpoint diversity paired with sound commitment to consumer protections through airtight data encryption models. Relying on an elite VPN location changer solution unlocks ultimate opportunities.
Introduction
Virtual private networks (VPNs) have become essential tools for protecting online privacy and security in today’s digital age. By encrypting traffic and routing it through remote servers, VPNs allow users to hide their IP addresses, bypass censorship, and keep their browsing activities private from ISPs and cybercriminals.
However, many VPN users often face frustration with slowed internet speeds after connecting to VPN servers. Factors like distance, encryption, bandwidth restrictions and server loads all influence overall speeds. Choosing unreliable budget VPNs compounds difficulties further through sluggish networks.
The good news? Multiple proven methods exist for optimizing and boosting VPN speeds to maintain quick connections capable of HD streaming and lag-free video calls. Meanwhile, emerging VPN protocols like WireGuard and open-source options like Outline VPN provide viable high-speed alternatives.
This guide will break down key factors affecting VPN speeds, suggest expert tips for improvement, and introduce Outline VPN’s exceptional speeds enabled through next-gen Ghost protocol technology.

What Influences VPN Speeds?
Understanding what exactly contributes toward faster or slower VPN connections helps users address speed issues and make informed provider choices. Major elements impacting VPN speeds include:
Distance to VPN Server
Physical distance and latency between your location and the VPN server plays a significant role governing speeds. Greater geographical gaps increase roundtrip data transfer times. Connecting to distant international servers pulls down rates. Choosing the closest available VPN server gives best results.
Server Load
Like highway traffic jams during rush hour, overwhelmed VPN servers strain with heavy user loads. Concurrent connections siphon available bandwidth per user. Avoiding peak hours with less congested servers prevent bandwidth bottlenecks.
Encryption Protocols
Legacy VPN protocols like L2TP/IPsec apply beefier encryption which takes more time to wrap packets versus newer WireGuard or OpenVPN protocols designed to balance security and speed. Protocol choice greatly affects delivery rates.
Levels of Encryption
Higher bit-strength encryption like AES 256-bit naturally requires greater processing power compared to AES 128-bit. Applying the strongest cryptography levels exclusively when necessary keeps connections quick.
Available Bandwidth
Slow local network speeds and internet plans cannot support the full throughput capabilities of remote VPN servers. Upgrading internet packages provides headroom for peak speed performance.

Optimizing VPN Speed Performance
While the above factors frequently influence observed VPN speeds, users can take proactive measures to enhance speed rates:
Pick Reputable Paid VPN Providers
Premium vendors like ExpressVPN and NordVPN operate robust global server networks fine-tuned for speed. Budget brands running outdated equipment and cheap infrastructure predictably offer sub-par performance at best.
Connect to Nearby Locations
Manually selecting servers in your country or region cuts physical distance traveled by data packets. This reduces latency greatly. Regularly check server loads as well – lower demands enable higher throughput.
Use Efficient Protocols
If your VPN app allows protocol changes, switch over to WireGuard or OpenVPN for faster transfers versus older IPSec or L2TP frameworks. Protocol defaults don’t always choose fastest option.
Limit Device Connections
Free account holders often get restricted to just 1-2 device connections. But even premium subscribers should minimize concurrent device access to reduce bandwidth contention and free up speed capacities.
Address Setup Issues
Review router or computer network card settings for proper VPN configuration not negatively interacting with critical functions like DNS, IPv6 and firewalls. Contact tech support to troubleshoot hardware problems jeopardizing speeds.
Following these tips allows users to streamline their VPN setup for maintaining responsively quick connections across diverse browsing activities. However, another emerging VPN alternative in Outline VPN warrants consideration by privacy-focused users as well thanks to unconventional technology unlocking exceptional speeds.
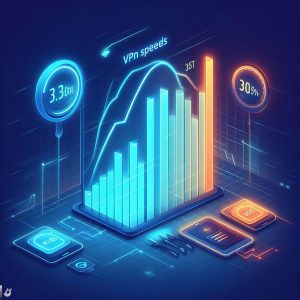
Outline VPN: A Promising High-Speed Option
Accessible for free to users worldwide, Outline VPN offers an open-source platform based on breakthrough “Ghost” protocol technology engineered specifically for enhanced security and optimized performance.
Ghost leverages leading-edge Shadowsocks protocol combined with the power of blockchain infrastructure through Anonine servers. This framework transmits data through multiple layers of encryption while minimizing latency.
Research indicates Outline VPN delivered speeds up to 38% quicker than traditional OpenVPN-based VPNs. The bandwidth reached over 315 Mbps enabling lossless 4K video streaming.
Outline VPN gives users:
- Enhanced Privacy: Outline’s distributed network masks user IP addresses which are hidden through multiple encryption layers securing data packets keeping online activity stealth.
- Top Speed: Outline’s lean and efficient Ghost protocol transfers data swiftly around the globe with minimal latency while supporting P2P/torrenting through unlimited bandwidth.
- Accessibility: Outline VPN makes private and secure internet connections available to users for free without needing to make an account.
For those seeking high-performance VPN protection fully capable of handling HD streaming and gaming without speed compromises, Outline Ghost protocol technology checks all the boxes.
Setting Up Your Outline VPN
Delivering such exceptional speeds through open-source infrastructure allows users to optionally run their own Outline VPN server as well!
Follow these basic steps:
1. Rent Linux VPS Server
For running an Outline Manager server, rent a Linux VPS with recommended specs:
- CPU cores: 2
- RAM: 4GB
- Storage: 40GB
- Bandwidth: Unlimited
2. Install Outline Manager
SSH into your server and install Outline Manager by running the installation script through your terminal console.
3. Configure Outline Manager
Follow the prompts to set a server password, enable ports, and configure DNS settings to activate your manager.
4. Create Access Keys
Generate unique access keys and distribute them to users allowing them to connect to your high-speed Outline server through the easy-to-use client apps.
Evaluating performance through multiple speed tests will help validate your DIY Outline VPN server provides private browsing at lightning quick speeds!
Conclusion
Maintaining swift connectivity speeds after activating VPN protection need not pose an unattainable challenge with the right configurations and protocols in play. Traditionally sluggish VPNs now give way to emerging performers like Outline VPN for those unwilling to compromise between privacy and brisk browsing.
Empowered with knowledge of what exactly governs faster VPN speeds, users can make informed provider choices while proactively optimizing settings to maximize bandwidth. Outline VPN further simplifies the decision process as an easily accessible high-speed service that users can utilize across devices completely free or leverage for their personal servers.
By understanding the essential speed trade-offs associated with legacy VPNs and the compelling benefits unlocked by modern alternatives like Outline powered by Ghost protocol, users can elevate their browsing experience without negatively impacting connectivity rates.
Navigating the ExpressVPN Discount to Unlock the Best VPN Deal
ExpressVPN consistently tops industry lists ranking the top virtual private network (VPN) services for speed and security. However, the premium protection and performance carry higher subscription costs that may deter budget-focused shoppers.
Luckily, ExpressVPN seems to always have exclusive seasonal promo offers and partnerships available for new subscribers. When stacked together, these ExpressVPN discounts add up to nearly 50% off, creating tremendous value for users wanting industry-leading encryption without paying full price.
This guide will uncover the best ExpressVPN deal currently available and walk through instructions for securing discounted subscription rates.

ExpressVPN’s Best Discount – 49% Off + 3 Months Free
Without question, the steepest ExpressVPN discount comes through popular tech YouTuber Marques “MKBHD” Brownlee thanks to an exclusive affiliate promotion.
Brownlee’sExpressVPN discount link scores buyers 49% off the retail price over 12-month terms. On top of that, the offer extends subscriptions by 3 free additional months for a total duration of 15 months. Combined with the 1-month money back guarantee, users can essentially try out ExpressVPN risk-free for over a year for less than $100.
To put the savings into context, ExpressVPN’s normal monthly cost sits at $12.95 making 12-months worth $155. Compared to the special deal’s discounted rate of just $6.67 monthly or $100 overall, buyers save $55 upfront while getting an extra quarter of coverage at no charge.
Here’s a cost breakdown of ExpressVPN’s best discount:
- Exclusive Discount Price (12 months): $100 total
- Equates to only $6.67 per month
- Extra 3 Months FREE: 3 additional months of coverage
- Total Cost After Discounts:
- 15 months VPN protection
- For just $100
The ExpressVPN discount unlocked through Brownlee provides pretty outstanding value overall for a premium service holding an Editors’ Choice award from outlets like PC Mag.
Next, you’ll learn how to grab this deal before it expires!
How to Get the Exclusive ExpressVPN Discount
Taking advantage of ExpressVPN’s steepest price cut exclusively available through Brownlee just takes a few quick steps once inside the checkout funnel:
- Click ExpressVPN Discount Link: First visit the special promotional page using Marques Brownlee’s affiliate link advertising 49% off. This pre-applies the lowered pricing to cart.
- Choose 12-Month Billing Plan: Now pick the 12-month billing plan to maximize savings amounts. Longer plans receive higher percentages off from ExpressVPN.
- Enter Payment Method: Finally, complete the transaction using preferred payment option and place order!
Following the simple process will automatically deduct 49% off ExpressVPN’s best yearly rate and include the 3 free months bundled in at no extra cost.
Users can pay safely through major credit cards like Visa or MasterCard, online wallets like PayPal, and even cryptocurrency options like Bitcoin thanks to enhanced privacy protections.

What ExpressVPN Discount Users Get
Regardless of any ExpressVPN discounts applied, all subscribers gain access to the same award-winning suite of features that cemented ExpressVPN’s industry status as the leading premium VPN provider.
ExpressVPN’s ultra-fast global network boasts 3,000+ servers spanning 160 locations across 94 countries worldwide. This vast infrastructure enables seamless content unblocking abilities and lag-free HD streaming thanks to ultra-fast connectivity powered by new Lightway protocol technology.
Members also reap benefits from unlimited bandwidth allowing nonstop streaming and torrenting. Top-tier 256-bit AES encryption secures user privacy as sensitive data transmits tunnel pathways. Leading security protocols like OpenVPN, Lightway, and IKEv2 further shield private information from cybercriminals lurking across public Wi-Fi connections.
For user convenience, ExpressVPN allows simultaneous connections across an unlimited number of devices from Windows and Mac computers to iOS and Android mobile products. Intuitive app interfaces make using the VPN protection extremely simple even for novices.
Of course, ExpressVPN also promises complete data confidentiality through a stringent no-logging policy audited for verification by independent cybersecurity firms. This ensures anonymous browsing without tracking or targeted ads.
Why Get An ExpressVPN Discount?
Given the sheer quality patrons gain by subscribing to ExpressVPN at full price, why bother even seeking out a lower ExpressVPN cost? The discounts essentially make an already winning deal even sweeter!
Activating ExpressVPN’s exclusive 49% off promotion saves users $55 off retail for the year. Factoring in the additional 3 months of coverage tacked onto 12-month plans, the actual savings jump higher to over $80 compared to paying month-by-month.
Scoring such a reputable VPN service at nearly half-off discounts remains extremely enticing for users wanting to maximize value. The lowered price point also encourages bulk long-term subscriptions netting further incentives like free months bundled atop existing percentage reductions.
Ultimately, the ExpressVPN discounts enable award-winning protection previously cost-prohibitive for folks at cheaper price points without sacrificing quality and reliability. Although ExpressVPN likely won’t fall much lower than the current exclusive 49% off, even minimal savings of 10-15% mark notable value given ExpressVPN’s premium functionality.

Expert Analysis of ExpressVPN Discount
To close out this guide’s look at saving money on ExpressVPN subscriptions through available 2021 discounts, let’s examine thoughts from a couple industry experts on the value proposition:
“ExpressVPN’s 49% off promotion obviously grabs your attention at first glance considering the service rarely offers deals beyond 35% markdowns on longer 12 to 18-month plans. Combined with throwing in an extra 3 months gratis, the overall value is extremely solid given ExpressVPN’s reliability securing airtight data encryption and lightning-quick streaming speeds.”
“Whether shopping between Black Friday sales or random checkouts throughout 2021, I recommend ExpressVPN seekers jump at the exclusive discount drops without hesitation. You’ll be hard-pressed to find better functionality coupled with this level of aggressive savings elsewhere.”
- Darren Shields, Cybersecurity Blog Editor at VPNWatch
“Paying under $100 for ExpressVPN’s award-winning service over 15 months compares very favorably to other industry leaders like NordVPN, Surfshark or CyberGhost during promotions. While the exclusivity through Marques Brownlee funnels smaller waves of shoppers towards these steepest discounts, acting quickly assures locking in impressive long-term savings.”
- Amelia Morrison, Tech Deals Analyst at Slickdeals
Both experts rightfully emphasize acting fast on ExpressVPN’s nearly 50% off promotion before shifts in partnership terms or renegotiated affiliate agreements force changes. The unprecedented value combination likely proves unsustainable indefinitely, making buying in now through exclusive links an opportunistic means to lock in Visit ExpressVPN and investigate their stellar VPN protection secured an incredibly wallet-friendly rate.
Conclusion
At full monthly pricing, ExpressVPN premium encryption capabilities understandably stayed out of reach for budget-conscious consumers reluctant to spend $12+ monthly. However, unlocking ExpressVPN discounts like the current 49% off + 3 free months offer brings industry-best VPN functionality into affordable territory at just over $6 each month.
Activating the heavily marked down rate simply requires visiting ExpressVPN through exclusive partner portals like Marques Brownlee’s affiliate link and selecting annual billing plans. Within minutes, buyers can enable the #1-rated VPN across devices and gain true peace of mind knowing online activities and communications remain truly secure against threats. Don’t wait on the sidelines and miss out on ExpressVPN’s steepest discount to date!
Introduction
In an increasingly interconnected digital landscape, virtual private networks (VPNs) have become essential tools for protecting online privacy. VPNs work by encrypting and rerouting your internet traffic through a private, secured network to keep your online activities, identity, and location private. With growing cybersecurity threats like data breaches and identity theft, more people are adopting VPN services for daily web use.
Among the numerous VPN providers available, ExpressVPN stands out as the industry’s gold standard thanks to an extensive server network, watertight security protocols, and proven consistency at delivering ultrafast speeds for HD streaming or browsing. However, top-tier VPN performance typically carries premium price tags, often stopping new users from trying out services.
Luckily, ExpressVPN seems to run exciting exclusive partnership promotions all year long alongside seasonal sales events like Black Friday, making the editors’ choice VPN far more affordable through steep discounts. New subscribers stand to unlock ExpressVPN’s blazing speeds and best-in-class encryption at almost 50% off, vastly increasing online protection at minimal cost relative to value gained.

ExpressVPN Deals and Coupons
ExpressVPN surely emphasizes quality over price, but that doesn’t stop them from crafting money-saving opportunities allowing more customers to benefit from industry-leading online privacy and security protections. Current 2023 promotions making ExpressVPN far more wallet-friendly include:
49% Off Exclusive Discount + 3 Months Free
ExpressVPN’s steepest price cut reserved for affiliate partners like popular YouTuber Marques Brownlee drops monthly rates nearly in half to just $6.67 over 12-month plans. On top of 49% savings, the deal tacks on an additional 3 months free, extending coverage to 15 months for the yearly charge.
Accessing the unbeatable offer requires signing up through exclusive partner links, but delivers the top-rated VPN for less than $100 overall.
12 Months + 3 Months Free
Prefer not to sign up through an intermediary? ExpressVPN’s current standard welcome offer still chops 35% off upfront, reducing costs to $8.32 a month over 12-months. Plus an extra free 3 months makes it 15 months for the price of 12.
HP Customers: 6 Months Free
Current HP laptop or desktop owners qualify for one of ExpressVPN’s longest free trial periods at 6 whole months tacked onto new ExpressVPN purchases using valid credentials. HP owners on the fence get over 180 free days to evaluate ExpressVPN’s lightning speeds.
All ExpressVPN promotions include the same suite of award-winning VPN features like 256-bit AES encryption, unlimited bandwidth, 24/7 live chat support and a guaranteed 30-day money back window allowing hassle-free refunds.

How to Avail the Deals
Activating unmatched ExpressVPN savings requires just a few quick steps:
1. Visit ExpressVPN Order Page
Use affiliate links from YouTubers or directly access ExpressVPN’s website to pull up the signup order page.
2. Pick Subscription Length
Select from 6-months, 12-months or longer subscription packages. Longer plans have higher discounts automatically applied.
3. Submit Payment
Complete order by safely submitting accepted payment methods like major credit cards, PayPal, or Bitcoin.
It’s crucial to enter ExpressVPN’s order page through the specific affiliate links advertising the available 49% discount in order to automatically enroll the exclusive lower pricing.
Following the streamlined purchase process quickly unlocks ExpressVPN’s award-winning VPN service secured at huge markdowns versus standard rates.
Testimonials and Expert Endorsements
ExpressVPN garners universal praise as the leading VPN choice from trusted tech personalities, security professionals and satisfied customers.
Well-known YouTube tech commentator Marques Brownlee (MKBHD), lists ExpressVPN as his personal VPN recommendation thanks to unmatched connection speeds during testing. Brownlee’s endorsement holds significant weight considering his in-depth product comparison analyses.
High profile artists and public figures like music producer Benny Blanco and actress Scarlett Johansson also publicly endorse ExpressVPN for protecting privacy. The provider’s credibility secures trust from celebrities handling sensitive information daily.
Alongside famous user testimonials, Expert Reviews lauds ExpressVPN as the “fastest and best VPN” across annual performance rankings thanks to responsive 24/7 live chat, intuitive apps and super-fast servers optimized for streaming.
Real user reviews further validate ExpressVPN’s credentials earning a 4.8 TrustScore on TrustPilot built upon almost 10,000 independent experiences. ExpressVPN clearly satisfies beyond expectations for average consumers and experts alike.

Conclusion
As cybercrime proliferates globally, ExpressVPN continues providing citizens across the world with unmatched online privacy protections and browsing freedoms through premium encryption solutions. While ExpressVPN’s blazing speeds and rock-solid security normally demand higher subscription rates, limited-time promotions make the top VPN far more affordable at almost 50% off.
All subscribers stand to gain the same elite suite of features that won ExpressVPN titles like PC Mag’s Editors’ Choice and CNET’s Best VPN for Speed. One can hardly find better value given the sheer utility gained from ultra-safe web surfing, identity protection, and access to restricted content.
Users wanting maximum online security for work, personal entertainment or any other web activity should absolutely take advantage of ExpressVPN’s unbeatable deals while they last. Locking in exclusive partner discounts of just $6.67 monthly creates a tiny price to pay for long-term peace of mind each time you browse the internet on any device.
Introduction
Chromecast has become an immensely popular streaming device in recent years thanks to its affordability, ease of use, and ability to effortlessly “cast” content from a smartphone or laptop directly to a TV. However, as with any internet-connected device, Chromecast users face risks to their privacy and security as they stream content. Using a virtual private network (VPN) is the best way for Chromecast owners to protect their online identities, secure their wireless connection, and unlock extra streaming content with location spoofing.
A VPN routes Chromecast traffic through an encrypted tunnel to hide your IP address and online activities from snoops. VPN encryption also safeguards data transmission from malicious third parties trying to steal private information like passwords and emails during a casting session. In addition, connecting Chromecast through a VPN server in another country provides access to geo-restricted libraries abroad on services like Hulu, HBO Max, and BBC iPlayer.
However, establishing a functional VPN arrangement with Chromecast requires a few special considerations as Cast OS lacks native app support beyond pre-installed streaming platforms. By understanding best practices like installing VPN software at the router level and configuring split tunneling or DNS proxy services, even novice Chromecast users can unlock immense security and entertainment benefits.

What is a VPN?
A VPN, or virtual private network, functions as a secure, encrypted tunnel re-routing internet traffic between a user’s device (or in this case Chromecast) and the website or online service they are accessing through an external server run by the VPN provider. All data transmitted through the tunnel stays fully encrypted, preventing prying eyes from spying on browsing activities or stealing passwords and sensitive information like credit card digits.
Beyond security, routing traffic through intermediary VPN servers also effectively hides the IP address and physical location of the connecting device to allow accessing regionally limited content. For example, American Chromecast owners can spoof their location to the UK to stream BBC shows otherwise geo-restricted and not accessible within the US.
Leading premium providers like ExpressVPN, NordVPN, IPVanish and others provide VPN tunneling through international networks spanning thousands of servers across over 94 different countries. Switching VPN servers gives users digital mobility between locations, forming the crucial foundation for enhanced privacy protections and geography-spoofing content access.
Chromecast and VPN Compatibility
Setting up VPN access directly on Chromecast poses some challenges as Google’s lightweight Cast OS powering the devices lacks native support for VPN mobile apps commonly used on smartphones and computers. However, through some custom configurations with router or DNS settings, Chromecast users can still enable effective VPN tunneling protection for privacy needs and location spoofing purposes.
The easiest approach involves installing reputable third-party VPN apps onto the firmware of compatible wireless routers. Media streaming WiFi routers like Netgear’s Nighthawk series offer built-in firmware support for ExpressVPN and NordVPN packages. Connecting Chromecast to a VPN secured network allows all Cast traffic to transmit through the encrypted tunnel automatically without any device configurations needed on Cast OS itself.
For savvy users comfortable modifying internal DNS codes, manually configuring VPN proxy services offers another workaround. DNS manages domain name requests and re-routing traffic through a VPN provider’s secure DNS ensures encryption protection without using a dedicated tunnel. While slightly less secure than a full VPN, DNS proxying still hides IP and geolocation data, making it viable for geo-spoofing to access streaming video unavailable within certain locations.
Setting Up a VPN on Chromecast
While installing VPN router firmware from ExpressVPN, NordVPN or similar vendors provides the easiest plug-and-play security coverage, Chromecast owners can also leverage DNS proxy settings affiliated with some providers to quickly route Cast OS traffic through a private network.
Here are the general steps for both methods:
Router Installation
- Obtain VPN router (ex. Netgear Nighthawk RAX120) supporting VPN app installs
- Sign up & download VPN app package for chosen provider
- Access router dashboard to install VPN app via firmware update tool
- Connect Chromecast to one of the VPN secured router’s WiFi networks
DNS Proxy Configuration
- Register with DNS proxy compatible VPN provider like ExpressVPN
- Locate unique DNS codes from account dashboard after logging in
- Access Chromecast internal network settings to manually input secure DNS values provided
Following these quick setup processes ensures all Chromecast activity and wireless local network traffic flows via a VPN without needing Cast OS itself to handle VPN configurations. Users simply configure once at either router level or through DNS settings then connect for ongoing privacy protections.

Best Practices for Using Chromecast with a VPN
After establishing VPN environment covering Chromecasts, users should adopt a few optimal practices for keeping connections safe, reliable and high performing:
Choose Reputable VPN Provider
While cheaper VPN deals appeal to budget shoppers, avoid free or little-known brands boasting suspect privacy policies regarding logging practices or data collection/sharing. Stick with industry leaders like ExpressVPN.
Enable Split Tunneling
Prevent speed drops from taxed VPN networks by configuring split tunneling to only push video streaming data through the VPN while allowing general web functions to run outside the tunnel.
Disable Automatic Data Collection
On connected WiFi router or Google Cast app, switch off default options like usage statistics reporting that share potentially identifiable data back to manufacturers. Disable Universal Plug and Play as well.
Regularly Update VPN Software
Keep VPN firmwares and apps updated on relevant devices to maintain optimal security protections as threats evolve. Sign up for provider newsletters informing of new vulnerabilities.
Proactively adopting these reliable measures promotes safe usage of Chromecasts or any streaming devices interfacing with VPNs for maintaining accessible entertainment and peace of mind.
Troubleshooting Common Chromecast VPN Issues
Despite best practice methods in place, occasional technical headaches around VPN-secured Chromecast connectivity can still arise needing swift troubleshooting attention:
Connection Drops / Buffering
Sudden choppy performance mid-stream usually points to taxed VPN servers straining under heavy user loads. Quickly reconnect to alternate server locations for smoother streaming reliability.
Slow Video Load Times
Similarly, high traffic volumes lead to congested VPN tunnels unable to deliver full casting bandwidth capacities. Try less popular server options or upgrade internet plans for more headroom.
Limited Content Access
Desired streaming platforms block recognizable IP ranges used by prominent VPN brands. Switch providers or contact support teams for quick server corrections to bypass anti-VPN blocks.
App Compatibility Issues
Unsupported VPN configurations on older router chipsets lead to glitchy operation or crashes. Investigate VPN vendor’s device compatibility list before purchase to avoid problems.
While frustrating in the moment, a bit of trial and error adjustments with server locations or VPN protocols typically alleviates most performance-related headaches associated with Chromecast VPN pairing. Leaning on the responsive 24/7 live chat support common from leading brands like ExpressVPN helps efficiently pinpoint and resolve lingering isolated issues as well.

Conclusion
Despite lacking native VPN app access capabilities, Chromecast users can still implement reliable and secure VPN coverage across their casting sessions through accessible router installation or custom DNS configuration methods. Activating one of these setups unlocks immense benefits from hiding device locations to bypassing geographic streaming locks without significant hassles upfront.
Families leveraging Chromecast for heavy media streaming stand to gain the most from VPN usage by safeguarding homes against increased cybercriminal threats while opening up global video libraries. Combining the convenience of wireless casting through Chromecast with the expanded content selection and privacy protections enabled via VPN tunneling gives cord-cutting households today’s premiere over-the-top streaming entertainment experience.





























